The Globality platform is designed, engineered, built, and tested for security every step of the way.
Our product managers, engineers, and QA testers are trained to identify information security risks and concerns as they work, from whiteboard sketches to production code deployment. Our devops engineers then ensure that our secure code runs strong and true on resilient, redundant, and highly available infrastructure.
We peer-review, audit, and pen-test our products before and after they are released to production using an arsenal of manual and automated code scanners and vulnerability finders. Our tiered architecture provides multiple layers of protection, each nestled behind its own firewall. WAFs, IDS, and DLP systems complete this picture, resulting in a strong, secure, and resilient enterprise-grade offering.
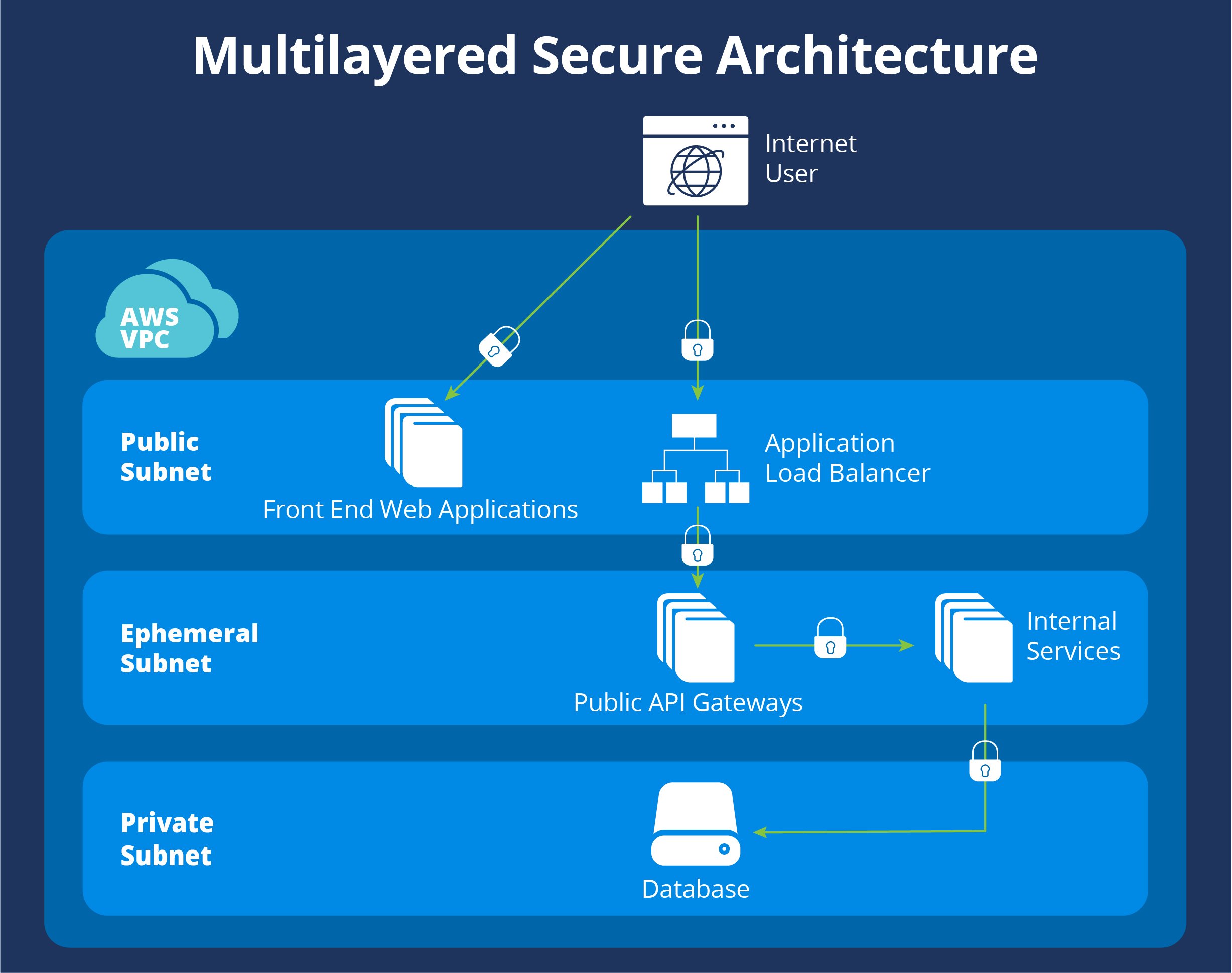
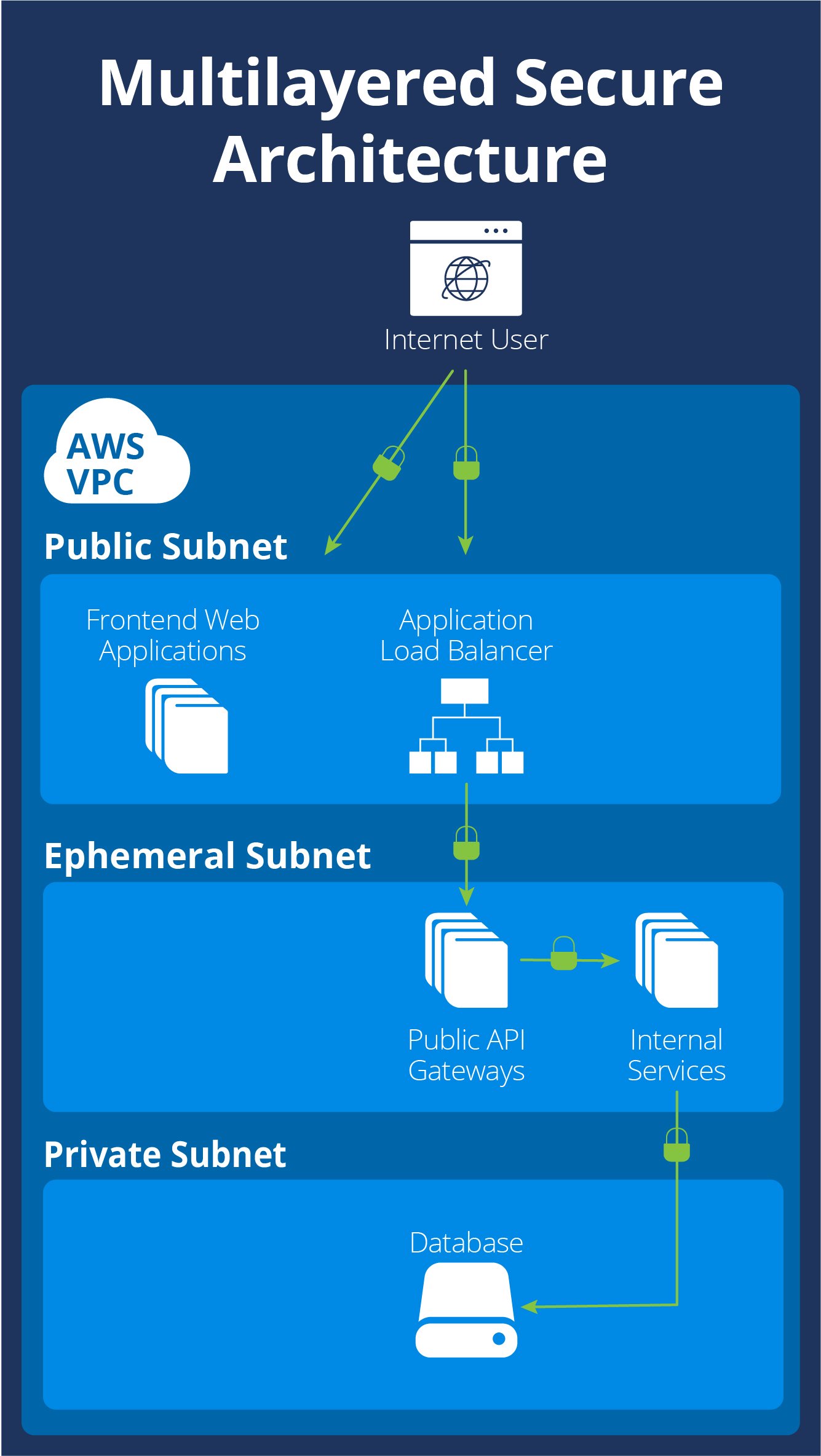
Globality maintains multiple identical, separate environments for development, testing, demo, and production. Each environment operates in its own silo, where components have access only to their immediate neighbors. For example, our data layer is accessible only to the services that control and handle data, never to our web servers, application servers, or network infrastructure.
The only part of the Globality platform that is publicly accessible over the Internet is our front-end load balancers, heavily protected by layer-3 and web application firewalls. Our web servers are safely situated behind those load balancers, protected by an additional firewall layer.
Globality protects its information systems from DDoS attacks using a combination of application-level performance-adjustment mechanisms and infrastructure-embedded technologies that are developed and maintained directly by our cloud service provider. We deploy intrusion detection systems (IDS) throughout our infrastructure and on any relevant instances and components. Our IDSs are configured to alert the information security team about any irregular use at the network or application layer.
Production resources are protected by dedicated controls with access limited to select individuals who are specifically trained, authorized, and continuously monitored.
Globality uses custom, pre-built images to create all its server instances. These images have been carefully constructed and configured to eliminate unnecessary services and are routinely patched to ensure minimal security risk.
A set of automated tools construct, configure, and populate our entire stack. They are restricted via individual session keys, to be used by authorized personnel only.
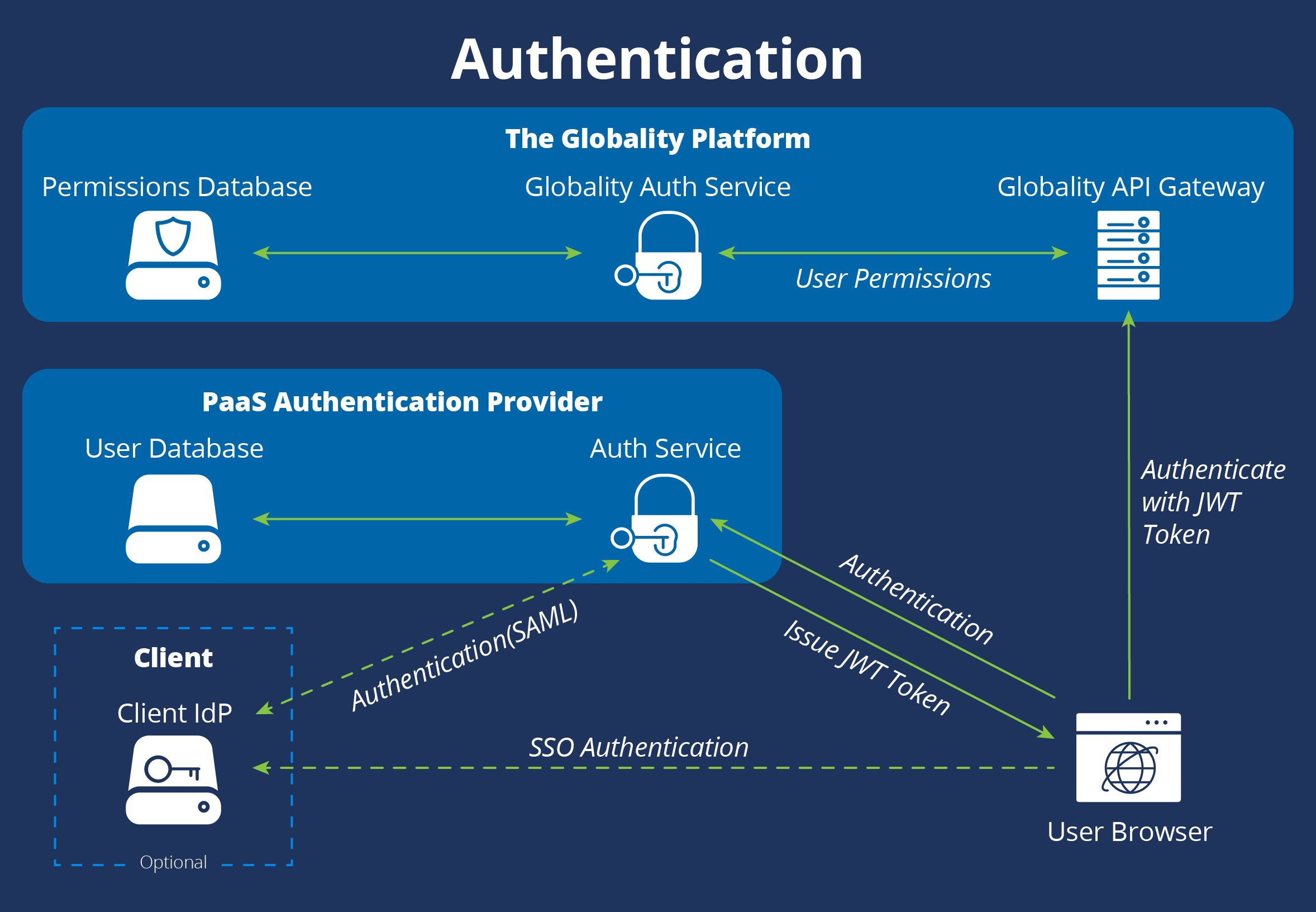
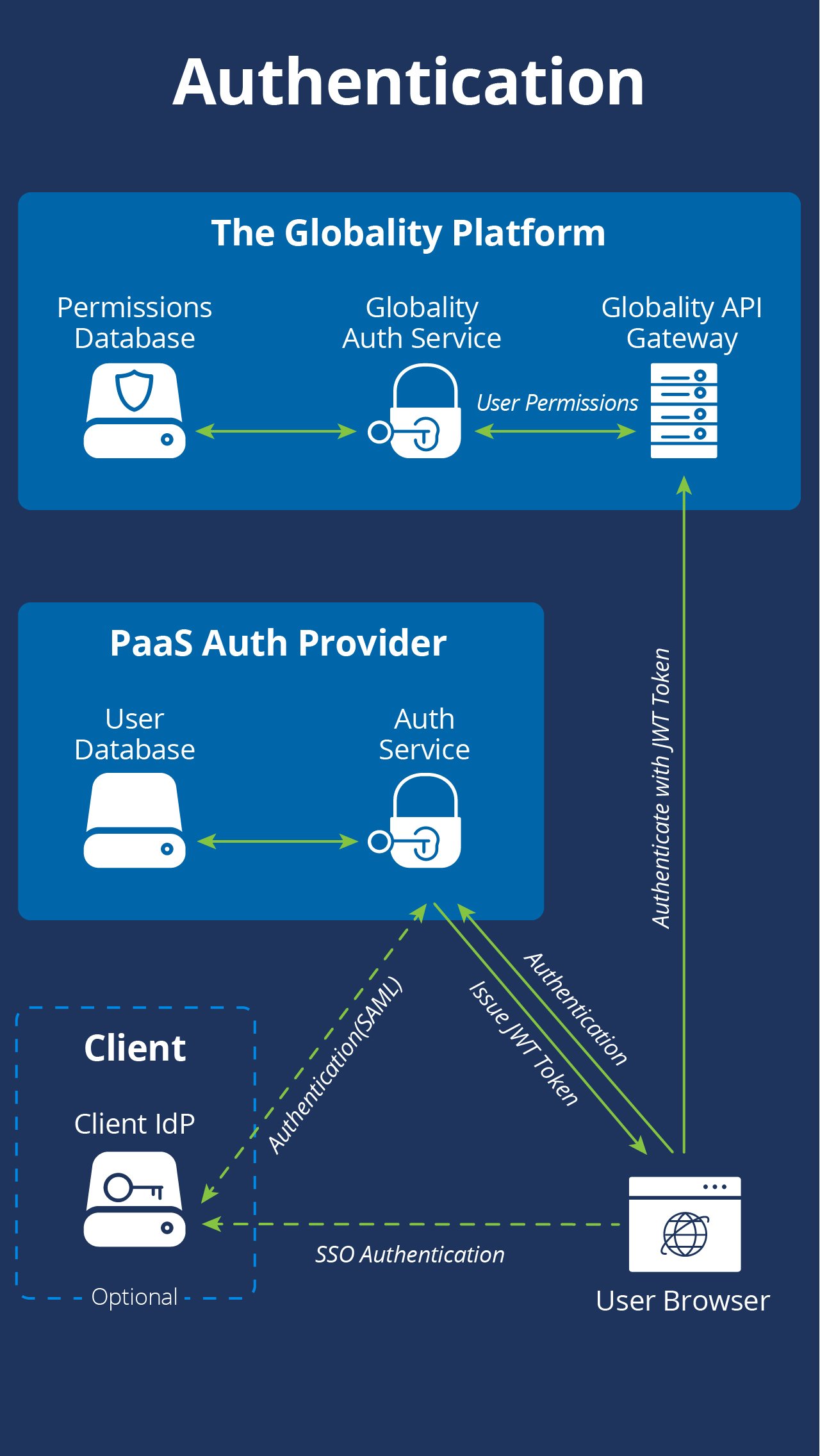
Globality supports several authentication options. Customers may elect to use a Globality-managed user/password database or leverage their own identity providers. Globality supports SAML (1.0 and 2.0) and Federation (ADFS) for a seamless single sign-on experience. Customers may also use SAML-compliant cloud-based IdPs such as OneLogin, Okta, PingFederate, SecureAuth, etc.
Customer data is categorized and access controlled at the specific URL and API call level using a combination of authentication, authorization, and entitlement mechanisms. A dedicated microservice supervises each and every request by validating it against its ACL database. User access objects are built on-the-fly and begin their authorization lives with the lowest default-level permissions.
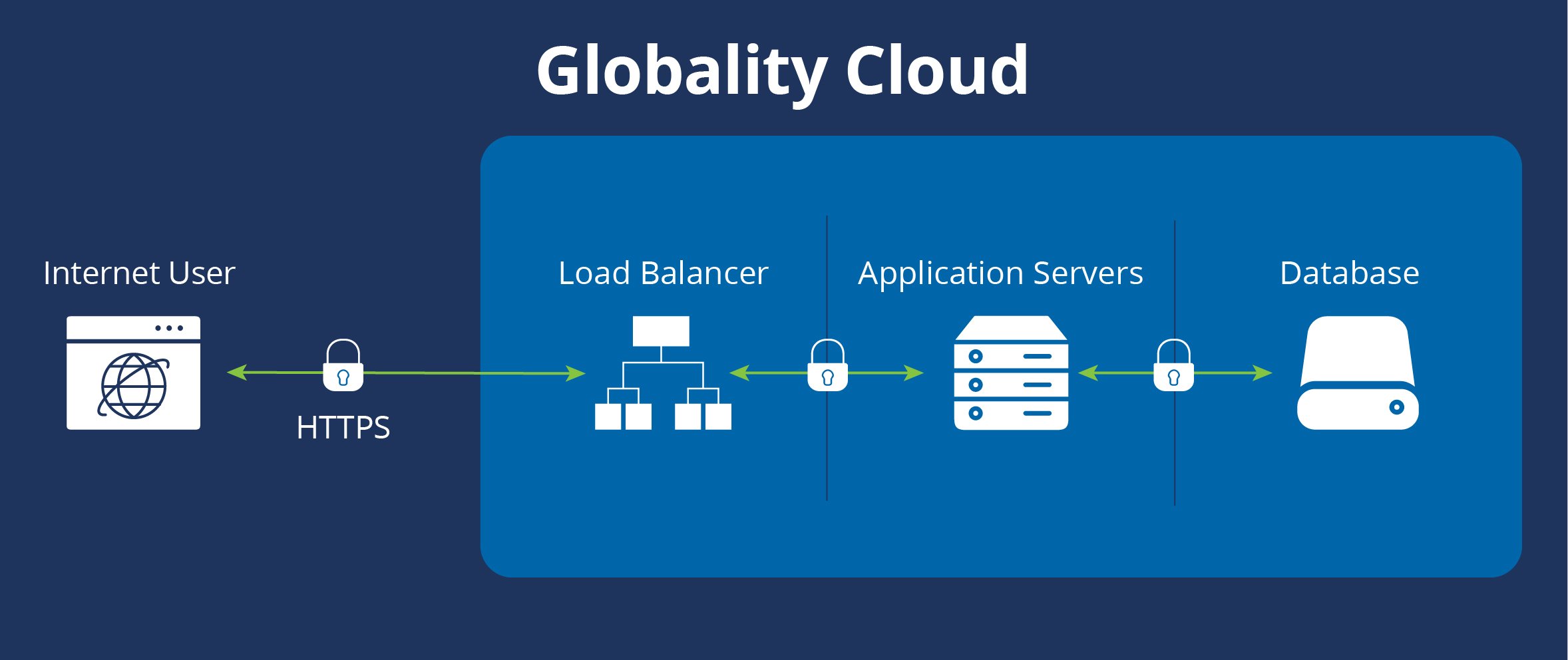
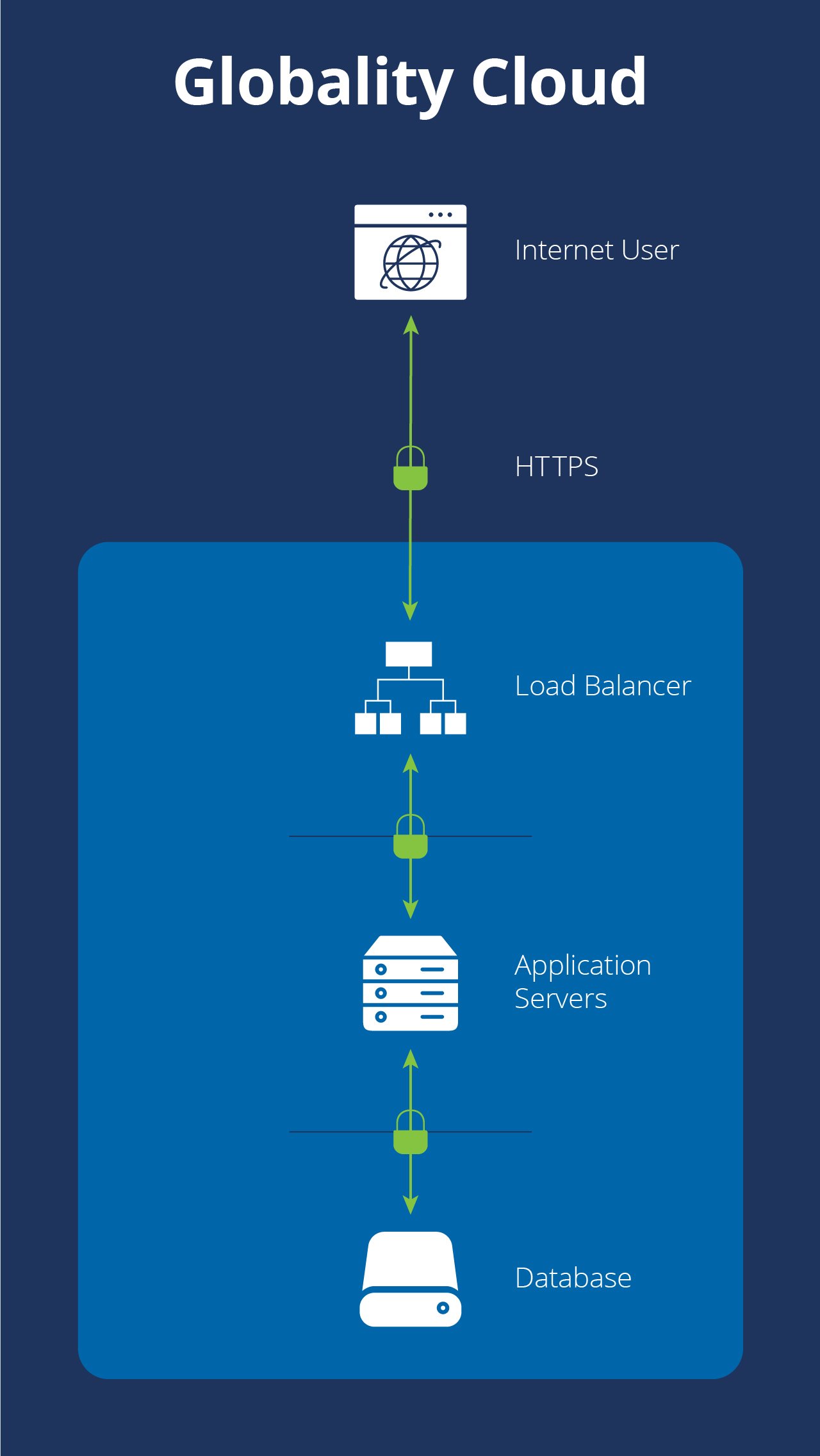
Any data transferred between Globality customers and our applications over the Internet uses industry-standard encryption. Globality uses the latest secure cipher algorithms to encrypt all traffic in transit, such as TLS 1.2+. Globality implements new encryption technologies as they become available.
Globality encrypts all customer data at rest using AES256 and a strong encryption key, stored in an HSM-backed Key Management System. The keys are delivered to processes at boot time, never written into any files, and are retained in memory only while in use. We use FIPS 140-2-compliant hardware to store our keys. Globality also offers application-level encryption and CMEK options. Please reach out for further information on this topic.
We fully support opportunistic TLS and will configure TLS enforcement for customers who request it.
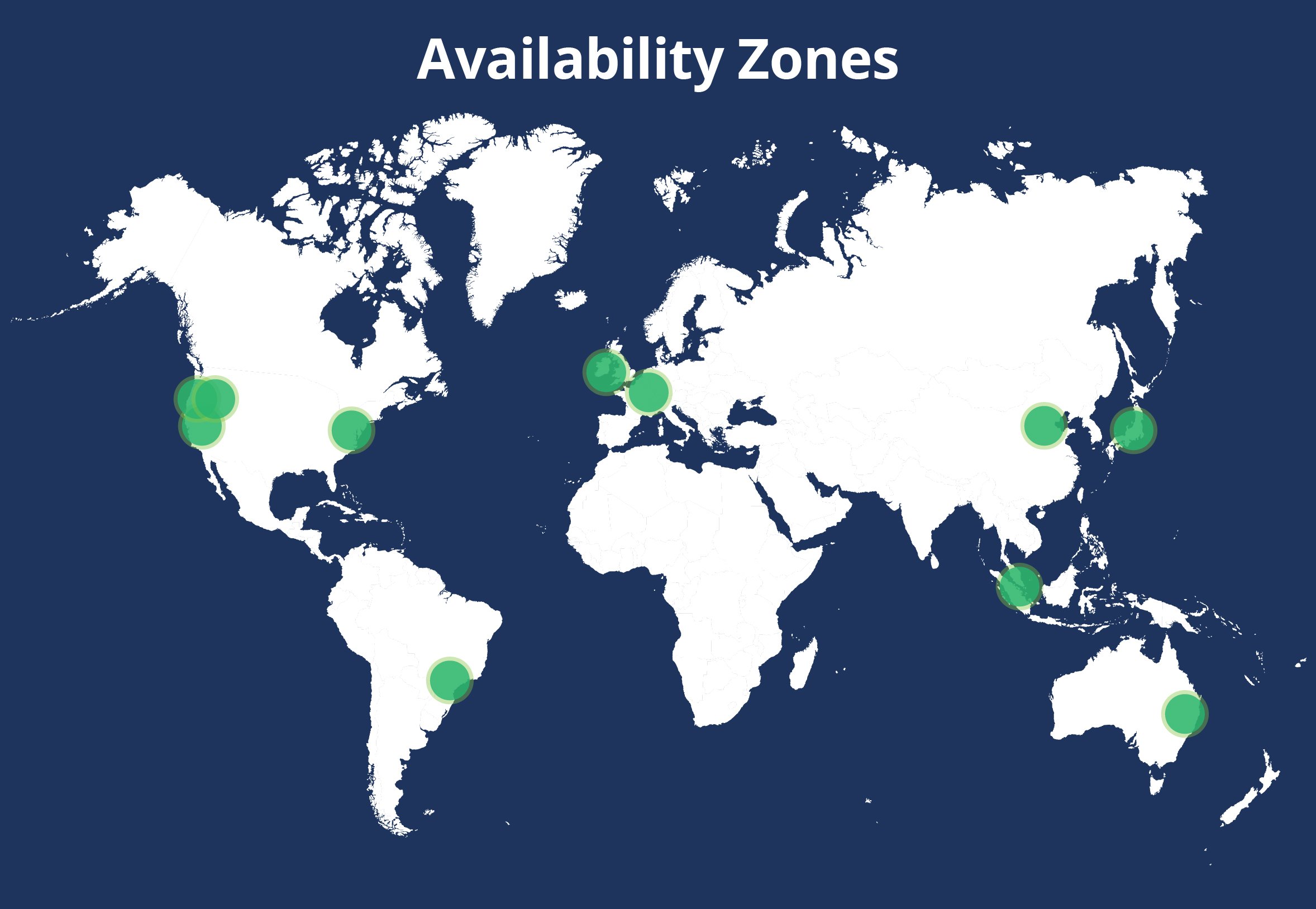
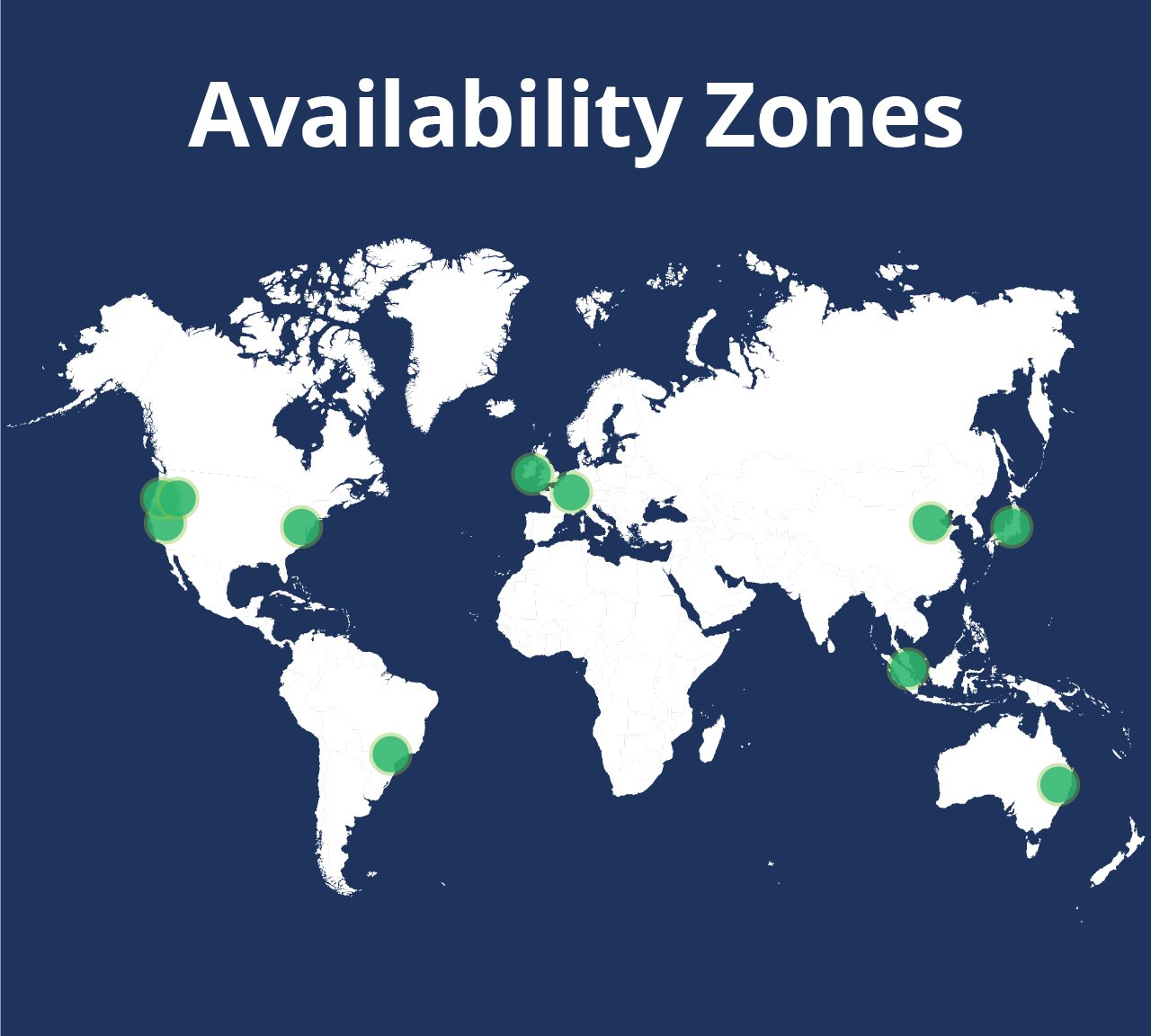
The Globality platform is built for enterprise business, and so is our infrastructure. Leveraging Amazon Web Services Availability Zones allows us to maintain multiple instances of our microservices in the air at any given moment and in multiple physical data centers. Were we to lose a whole data center, the remaining instances would continue serving requests with no impact to our users. Our auto-healing technology monitors instance health and activity and will automatically launch fresh instances when necessary to replace stale or failed ones.
Because our infrastructure consists of microservices running in containers, we can easily launch additional service nodes whenever our capacity approaches a peak. Bringing up a new microservice takes mere seconds, so users never encounter performance issues even during times of high demand.
Our infrastructure as code (IaC) approach allows us to launch our entire infrastructure in under an hour in any of Amazon’s worldwide regions. We conduct regular tests to ensure that we can quickly switch from the East Coast to the West Coast with no data loss.
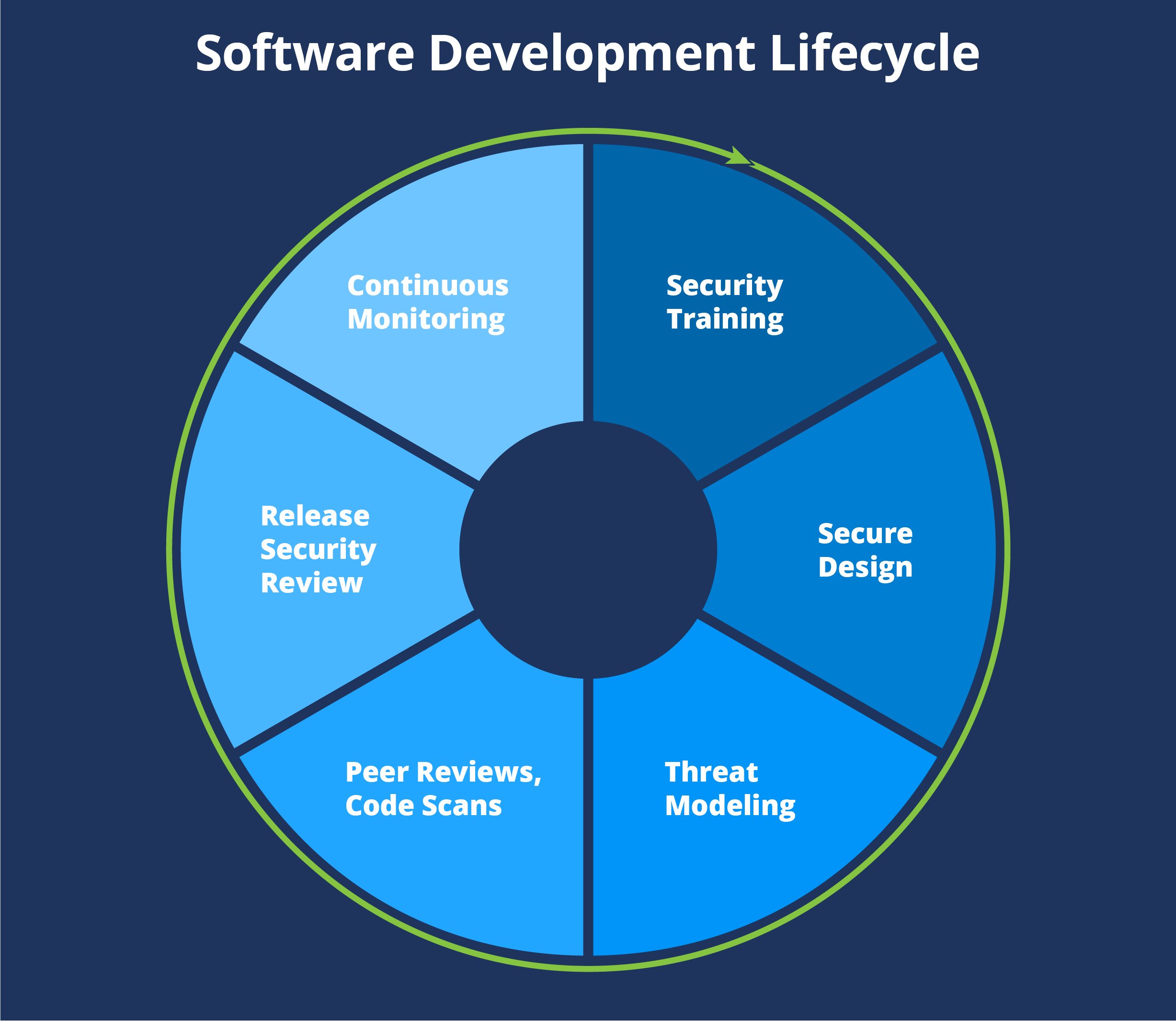
An integral part of each engineering project at Globality is a detailed security evaluation by the information security and engineering teams. Security implications of changes to code and infrastructure are considered and assessed per Globality’s SDL policies. The teams produce a set of recommendations that must be met before any feature or specific product is released to production. To detect potential vulnerabilities early on, Globality also makes use of multiple automated security tools to continuously scan its development and testing environments.
Globality applies strict change control processes to all production systems, including multiple automated and manual code tests on all environments. These procedures ensure that any changes that may impact customer data and data security are documented and approved before deployment.
When engineers are ready to submit new code to our repositories, they must get their submission reviewed by two other engineers, including at least one senior engineer, before it can be merged in. All code is continually scanned for vulnerabilities and misconfigurations to eliminate the possibility of introducing malicious code into Globality’s products.
Globality continually releases updates, feature improvements, and patches throughout the release lifetime. All releases are thoroughly tested, manually and automatically, before and after release.
We perform continuous and automated scanning of our infrastructure, code base, and environments to identify vulnerability or patch discrepancies. All code, and associated third party dependencies, are continually scanned for vulnerabilities and updated whenever an issue is detected. Findings are reviewed by our information security team and are classified based on their risk, impact, and criticality of data involved. We patch critical vulnerabilities in as little as 12 hours.
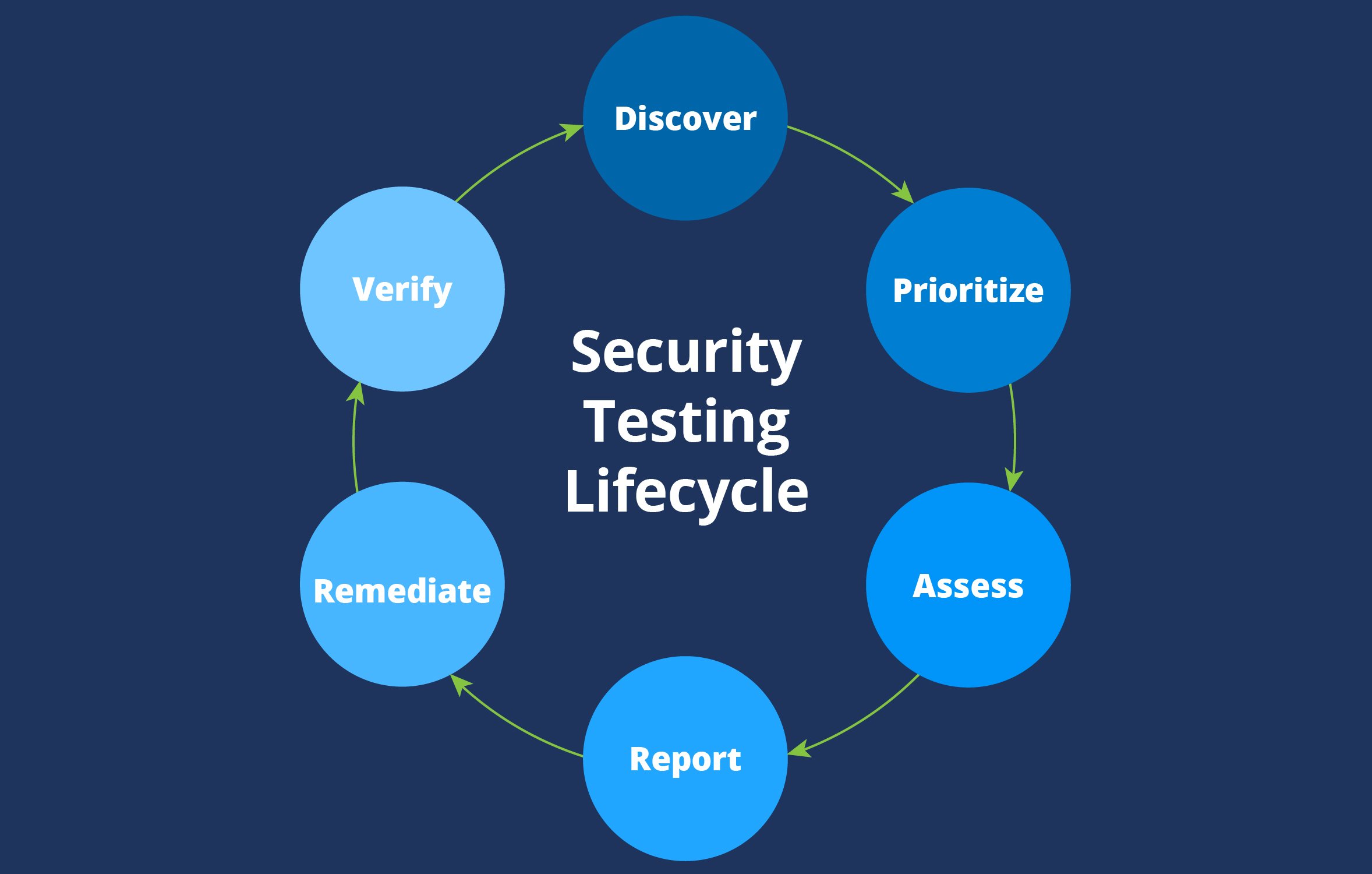
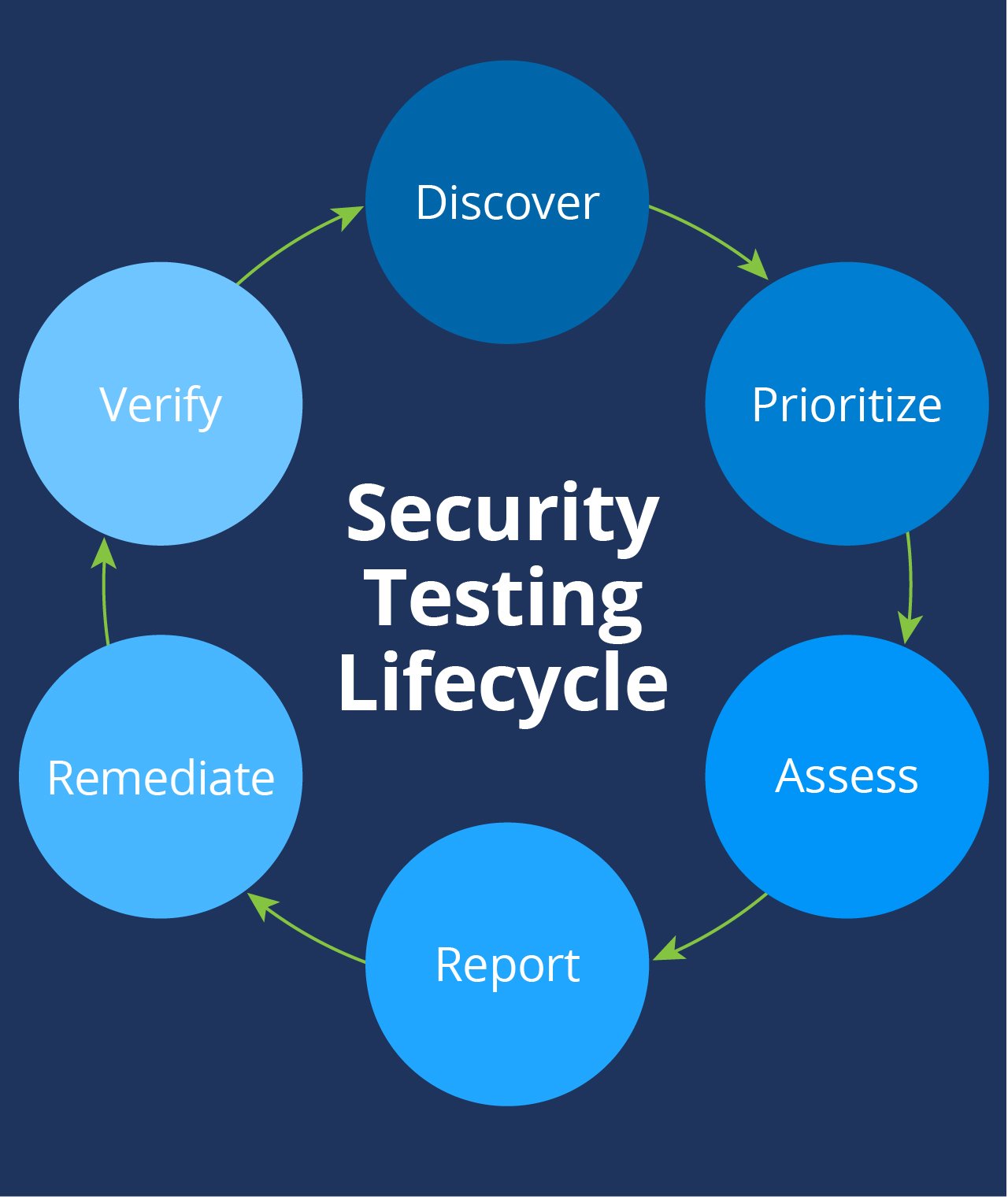
We continuously test our products for security flaws and potential vulnerabilities. Every line of code must pass tests in three different testing environments before it is ever exposed to our users. A combination of manual and automated tests ensures that our code is clean and lean. We hire external security professional to rigorously test our application at least annually and with every major release. Automated scanners inspect our publicly accessible endpoints and servers every 24 hours to detect zero-day vulnerabilities and will immediately alert our engineers about any high-risk issues.